Bugs and Issues
An advance cryptomining malware could be a threat to Huawei Cloud

An advanced version of crypto-mining malware has been found lately that could be a serious threat to Huawei Cloud and users. This malware was previously reported attacking the open-source software development platform- Docker Containers.
As per the report, this new malware version has enough algorithms to dodge the firewall rules creation function. Adding to this, it leaves a network scanner behind to track API-relevant ports of the other hosts.
However, this new crypto-mining malware is currently active in cloud environments. Furthermore, it’s checking for the other ecosystem that has previously been affected by this attack.
Before discussing its other details, let’s first know what crypto-mining is-
What is Crypto-mining :
Crypto-mining or Cryptojacking is defined as an online thread or malware that holds the ability to hamper and even crash an organization’s digital environment. In addition, it worked while staying completely hidden from a user.
In Cryptojacking, the attacker can use the victim’s devices without their concerns to secretly mine cryptocurrency. Likewise, it also causes financial losses for the victim and disruption to business workings. Moreover, it mainly targets cryptocurrencies or digital money.
On a Linux system, this digital currency miner malware has to follow a procedure shown in the figure. It not only harms the system but simultaneously removes its traces.
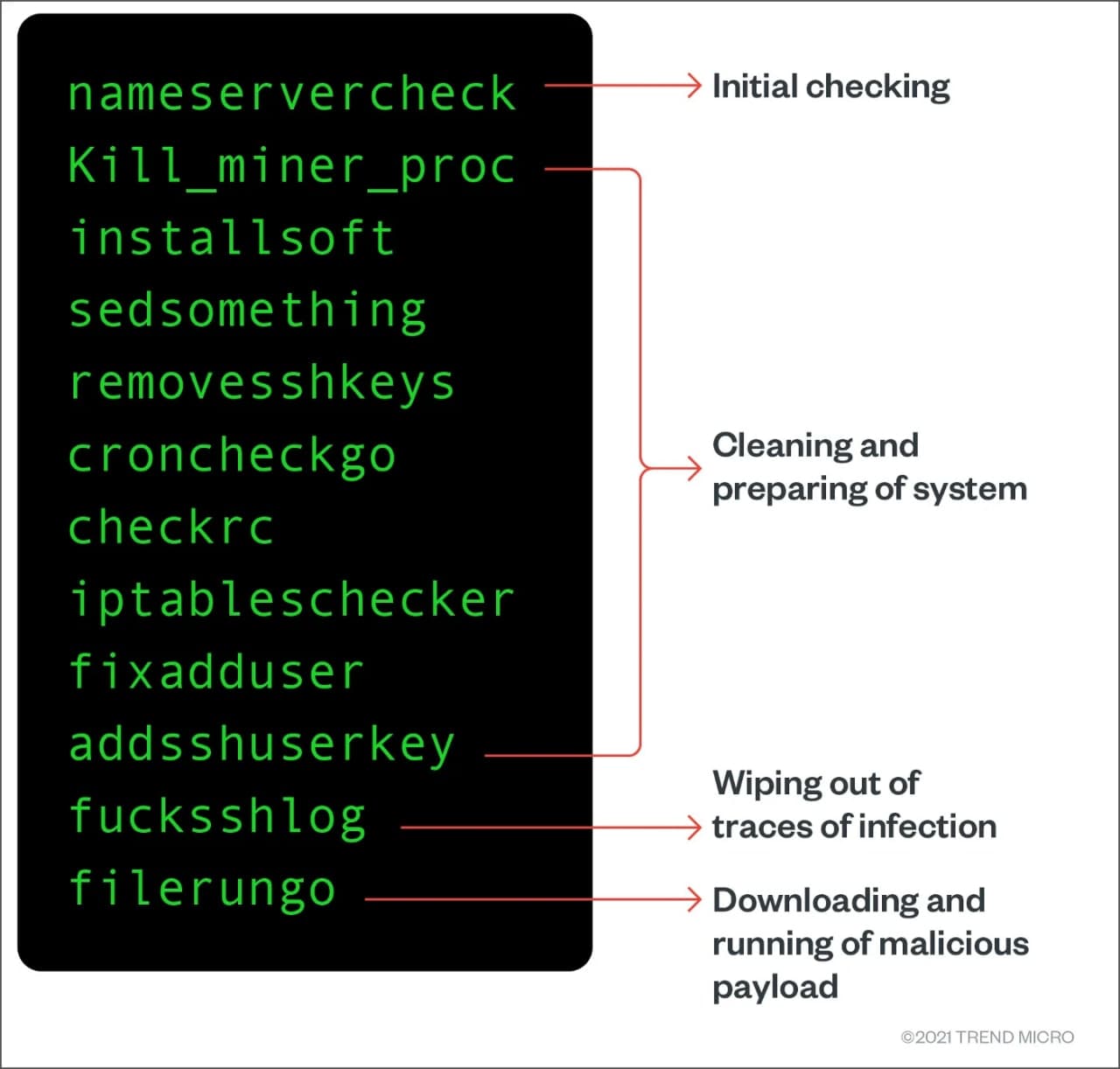
Afterward, it replaces all users added by the other actors with the one created by them. It’s one of the basic steps follows by the cloud-targeting cryptojackers. Unlike other attackers, the cryptojackers use the Sudo programs in their accounts that provide root access to the system.
Furthermore, the attacker uses their own sh-RSA key to perform system adjustments and change the file permissions to a locked state. It restricts other users to get entire control of the vulnerable computer or device even if they gain access to the device.
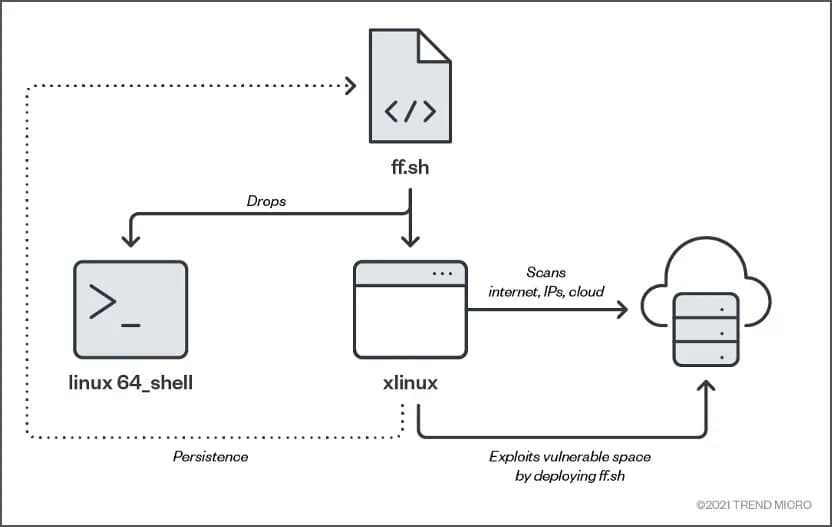
Besides, the actors install the Tor proxy service that helps them in preventing from establishing a connection to other network scanning detection. For wrapping, there are binaries codes (linux64_shell, ff.sh, fczyo, xlinux) at UPX packer. Once the attack get complete control of the device, it began to execute its malicious activities.

However, there are some known vulnerabilities detected during the scan in this attack. Most of them are related to the weak password in some functions that includes
Some Known Vulnerabilities:
- SSH weak passwords
- Vulnerability in the Oracle WebLogic Server product of Oracle Fusion
- Middleware (CVE-2020-14882)
- Redis unauthorized access or weak passwords
- PostgreSQL unauthorized access or weak password
- SQLServer weak password
- MongoDB unauthorized access or weak password
- File transfer protocol (FTP) weak password
As you can see, what users can if on Huawei Cloud if this coin-mining malware has been surfed in actual. To be mention, all the describe info came from the leading data security and cybersecurity solution provider TrendMicro.
According to this firm, it has sent the acknowledgment report to Huawei Cloud to make the authorities aware of the crypto-mining malware. Now, we are waiting for Huawei to officially address this problem.
(Via- BleepingComputer)






